
Introduction
Understanding how digital signatures work is fundamental to understanding how blockchain technologies work. Let’s first draw a comparison to paying a restaurant bill with a credit card.
Paying a bill at a restaurant
Think of what happened the last time you paid your bill at the restaurant with your credit card. Here is a snapshot:
- You pull the card from your wallet and you might have a photo ID on the card. This proves you own* the card.
- You sign the bill in front of the waiter. The proves you are the “rightful” owner of the card.
- You check the receipt against the bill. You prove that the amount charged hasn’t been altered somewhere in the process.
* It actually proves possession of the card but the entire process serves to illustrate a simplistic view and is not without it’s flaws.
These 3 points illustrate 3 key properties:
- Ownership. The card belongs to you.
- Transaction authentication and non-repudiation. The waiter can verify that the owner signed the bill and the owner cannot deny the signing.
- Data Integrity. The amount charged was accurate.
How can this be performed in a digital world where both parties hide behind a screen, do not know each other and therefore do not trust each other. Enter public/private keys.
Public/private keys
Back in the 70’s and 80’s cryptographers invented a way to fulfil the 3 key properties mentioned above. This is achieved by the use of what is known as a public/private key pair.
A public key is something that can be distributed or known to the public and the private key is something that the owner must keep securely. They are mathematically linked so that only the public key can decrypt what the private key has encrypted and vice versa.
How it works?
There are 5 steps involved:
- Generate a public/private key pair
- Create a message digest
- Encrypt the message digest with the private key to create a signature
- Append the signature to the document
- Place it on the blockchain
There are numerous tutorials on how this can be done. Here we outline the general process.
Step 1: Generate a public/private key pair
This can be done using software such as Putty for windows or via the ssh-keygen command for Mac or Ubuntu.

Step 2: Create a message digest.
We take some information we want to sign. This could be a house title, a will, digital rights to a song, or even a simple IOU and we run it through some software that applies a hash function and creates a message digest.
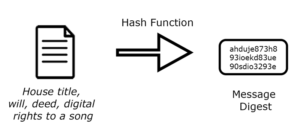
A hash function takes an arbitrary input and produces a seemingly random string of characters that is unique for that input. This is called the message digest. What this means is that if even one character is changed in the input, the message digest will be totally different. You should be thinking data integrity here.
Step 3: Create the signature
The message digest is then encrypted with the owners private key. The output of this is the digital signature.
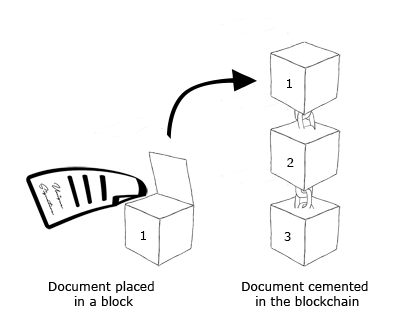
Step 4: Append the signature to the document
The signature is placed with the document.

Step 5: Place the document on the blockchain
This makes the document publicly available, because the blockchain is just a globally distributed, publicly accessible database. More importantly though, it timestamps the document effectively proving an event has occurred.
Using the public key
The public key can now be used by anyone to decrypt the digital signature to reveal the message digest. Successful decryption proves authenticity of the document. That is, does it really belongs to the person who is claiming ownership?
The integrity can also be determined by the receiver creating a message digest of the received document and comparing it to the digest provided within the document. If the 2 match, then the receiver can be confident that the message was not tampered with.

Summary
Ownership is provided by having the private key in your possession. This is why with blockchain technologies, the private key is so important. If this is compromised, you’re in trouble. Someone else could impersonate you.
The fact that the public key works means that the private key was used to sign the document and it also ensures non-repudiation. The owner of the private key cannot deny that they didn’t sign it.
The message digest ensures data integrity. In other words, the if the document has been altered, the public key would no longer work.
Now you can take any piece of information, such as a marriage certificate and understand how it all works on the blockchain.


Thank you so much … you are a great teacher.